Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
Advertisement
Scientific Reports volume 15, Article number: 4143 (2025)
Metrics details
Security in e-healthcare applications such as Telemedicine is crucial in safeguarding patients’ sensitive data during transmission. The proposed system measures the patient’s health parameters, such as body temperature and pulse rate, using LM35 and pulse sensors, respectively. The sensor data and the patient’s medical image are encrypted in the Raspberry Pi 3 B + processor using Python’s proposed text and medical image encryption scheme. The encrypted data is transmitted via the Thing Speak cloud and received by another Raspberry Pi at the receiver to decrypt the cipher data. The flask webserver can view the decrypted data by the doctor at the other end. This IoT implementation of secure Electronic Health Record (EHR) transmission employs text and medical image encryption schemes using a Combined Chaotic System (CCS). The CCS generates the chaotic key sequences to shuffle the medical image row-wise and column-wise. Then, selective shuffling between the cut-off points breaks the statistical relationship between the neighbouring pixels. Finally, the intra and inter-pixel diffusion is carried out using bit permutation and bit-wise XOR operation to create a highly random cipher image. The initial seed for inter-pixel diffusion is obtained from the hash of intra-pixel diffused images to resist chosen plain text and cipher text attacks. The efficiency of the developed medical image encryption algorithm is tested against various attack analyses. The results and the security analyses validate the effectiveness of the proposed scheme.
The Internet of Things (IoT) is an intelligent network framework that enables various heterogeneous smart devices to communicate with each other over the Internet. In scenarios such as the COVID-19 pandemic, doctors need to know about the patient’s health status without visiting the patient’s place remotely. In such scenarios, integrating IoT with the healthcare industry has significantly improved diagnostic procedures and the quality of e-healthcare. This high-quality diagnostic procedure requires many smart devices to be interconnected to collect the patient’s health information, such as blood pressure, oxygen saturation, body temperature, pulse rate and many more. The collected patient’s health information is difficult to store in IoT devices due to its resource-constrained nature1. Though on-premise storage may be secure and controllable, it often faces challenges such as high costs, limited scalability, and difficulty backing up data. In recent years, cloud computing has emerged as a popular alternative, widely adopted by enterprises to deliver services. For applications such as Telemedicine, the collected patient data must be transmitted from one place to another (i.e., from homecare/ remote clinic to specialised hospitals)2,3,4.
Cloud storage offers several advantages, such as scalability, reliability, and disaster recovery of data, and it is economically less expensive than on-premises storage. Therefore, the healthcare provider should depend on cloud or external storage to store the collected data. Consequently, storing the collected patient data in the cloud overcomes the difficulty of restricted data storage and provides data accessibility in a broader range. Cloud computing serves as a platform for storing data with varying levels of sensitivity, including public, internal-only, confidential, and restricted information, while providing customers with 24/7 access to computational resources. However, this extensive functionality makes the cloud susceptible to risks and threats from attackers seeking to exploit system vulnerabilities. Such attacks can compromise one or more of the core objectives of security: confidentiality, integrity, and availability5,6,7. The data security and privacy of the stored data entirely depend on the security policies of the cloud service provider8.
In healthcare IoT systems, transmitting patient data has essential ethical and legal implications, particularly concerning data security, privacy, and authorisation. Strict controls over the management, transmission, and storage of Personally Identifiable Information (PII) and Personal Health Information (PHI) are required by laws like the General Data Protection Regulation (GDPR) in Europe and the Health Insurance Portability and Accountability Act (HIPAA) in the United States. Adherence to these regulations is crucial for safeguarding patient rights. GDPR and HIPAA impose legal obligations on corporations regarding their handling of patient data9,10. HIPAA requires a secure transmission of data and mandates audits and documentation. GDPR has rigorous requirements for processing and transmitting data and introduces principles demanding that data protection be integrated into every aspect of data processing. HIPAA and GDPR require healthcare providers to implement measures that ensure data confidentiality, integrity, and security. Failure to secure transmission channels could lead to unauthorised access and breaches, exposing healthcare organisations to legal liability and potential fines. Hence, protecting patients’ sensitive data from hackers is essential. The best option to overcome this struggle is to encrypt the patient’s health information and medical images before transmitting them to the cloud storage environment.
Securing medical images using traditional encryption algorithms such as Data Encryption Standard (DES), Advanced Encryption Standard (AES) and Rivest-Cipher 6 (RC6) are inappropriate11. This is because of the intrinsic features of medical images, such as high redundancy, bulkier data and high correlation among the neighbouring pixels12,13. Traditional encryption algorithms require increased operations to conquer the intrinsic features of medical images, expanding the system’s complexity and overhead. Many conventional cryptographic algorithms came into the scene to break the stronger correlation among the pixels of medical images.
A few prominent techniques for medical image encryption are based on Linear Feedback Shift Register (LFSR)14,15,16, Cellular Automata (CA)17,18, Deoxy-ribo Nucleic Acid (DNA)15,19,20, chaotic maps21,22,23,24, compressive sensing25,26, transform domain approaches27, etc. The chaotic systems have several advantages, such as enhanced randomness, high ergodicity and non-uniform key distribution to trigger the potential cryptosystem. Many works based on 1D chaotic maps and higher dimensional chaotic maps are reported in the literature.
One-dimensional chaotic maps are simple and easy to implement28. However, the keys generated from 1D chaotic maps suffer from limited non-uniform distribution range and key space to resist brute-force attacks. Higher dimensional chaotic maps offer better key space and security29. Nevertheless, it struggles with high computation overhead and complexity. IoT devices employed in the e-healthcare sector are resource-constrained in nature. Hence, the security algorithms proposed to protect the patient’s privacy should be chosen with extreme care to support the nature of IoT devices. The trade-off between security and computational security should be maintained to reinforce effective implementation30. Witnessing the pros and cons of 1D chaotic map and higher dimensional chaotic maps, many researchers are attracted to combining multiple 1D chaotic maps in a single mechanism to boost security with less computational cost12.
Reference31. have accomplished an intra-inter pixel encryption scheme which involved multiple levels of permutation and diffusion based on a Piecewise Linear Chaotic Map (PWLCM). The intra-bit level permutation is executed parallelly in the bit planes to reduce the time complexity. This work is proven to resist various supreme attacks. However, the real-time implementation of an algorithm in an IoT environment is not discussed. Trujillo et al. have used a 1-D chaotic map to obtain improved random sequences to be XORed with the medical image stream, resulting in the cipher bits required for the Healthcare IoT domain32. The implementation used message queuing telemetry transport (MQTT) protocol to transmit medical images. Much information on the real-time implementation of H-IoT has not been provided. In addition, the key space is 2192, which is marginally less. Another work uses a deep learning approach to generate the keys to encrypt the medical image33. A RESNET-50-based architecture has been used to transform images. RESNET-50 achieved less time for encryption than standard encryption algorithms like DES, 3-DES, AES and RSA. However, the information on attack analysis is not carried out to check the strength of the developed model. A hybrid encryption algorithm with symmetric key algorithms such as AES for securing the data and an asymmetric key algorithm, namely Elliptic Curve Cryptography (ECC), for providing necessary authentication to the IoT environment is proposed by34. Preserving users’ privacy has been focused on in addition to healthcare data security in a H-IoT framework. The algorithm is secure against various attacks, such as man-in-the-middle, collision, and forgery attacks.
Reference35. have implemented a post-quantum cryptographic scheme to reap the combined benefits of code-based and lattice-based cryptography. Computational complexity and execution time have been reduced by a polynomial multiplication scheme with Bernstein reconstruction to suit the resource-constrained IoT devices36. implements a hybrid and adaptive cryptographic scheme with the encryption function using AES and ECC / RSA for IoT-based applications. The authors have achieved optimisation in terms of communication cost, computation time and memory. Ashutosh et al. have developed a tool for performing security analysis on the lightweight encryption algorithms SIMON and SIMECK ciphers specially designed as lightweight for IoT framework37. The authors found differential paths for the cryptographic function with less computational time. Mujeeb et al. have portrayed the synergy of multiple encryption techniques, namely alternate quantum random walks, DNA encoding, and controlled Rubik’s Cube transformations, along with integrating the Elliptic Curve Cryptosystem with Hill Cipher38. The authors have successfully tested the proposed technique on medical images of different modalities. The algorithm also efficiently resists statistical, differential and brute force attacks. Ravichandran et al. implemented a multilayer encryption scheme with the upper layer dealing with DNA coding combined with a chaotic map. Symbol-level encryption is achieved in the Physical layer with chaotic scrambling of the OFDM stream39. Ravichandran et al. chose to work in the Integer Wavelet domain, fusing a chaos algorithm with DNA coding in two phases: diffusion and permutation. The authors have proposed an efficient Electronic Health Records40 medical encryption technique.
The related works reported so far have developed image encryption algorithms suitable to work in IoT environments31,32,33,34,35,36,37,38,41,42,43,44,45,46. Though they can resist specific critical cryptographic attacks, it is essential to highlight that these works are not tested in real-time. Few works in the literature that use real-time testing in IoT environments with enhanced security are reported. Devipriya et al. derive the initial value for the chaotic map using a hash function on the input image and perform block level, pixel level and bit level shuffling supported by learning with errors-based diffusion47. The authors have contributed to a novel encryption scheme for IoT devices by modifying perfect shuffle algorithms to improve security. The algorithm has a key space 1069, and can resist statistical, differential and brute-force attacks. Raspberry Pi 4 Model B is chosen for real-time transmission of collecting images and performing encryption to secure the images. A fast encryption scheme based on a 5D fractional-order (FO) hyper-chaotic multi-scroll (HCMS) system is proposed by Daniel et al.41. The encryption scheme’s physical implementation is carried out on an Advanced RISC Machine (ARM) processor in machine-to-machine (M2M) communication, utilising the message queuing telemetry transport (MQTT) protocol. Qiang et al. have developed an image encryption scheme based on Integer Wavelet Transform (IWT), 3D hyperchaotic map and DNA coding for healthcare IoT systems. The scheme has achieved PSNR above 35 dB for the decrypted image encrypted using bit-level permutation and diffusion43.
It employs pseudo-random sequences generated by a novel 3D hyperchaotic map. Initially, IWT is applied to extract the approximation components of the images, followed by a novel diffusion algorithm that masks critical information. A bit-level permutation mechanism further enhances encryption complexity by rearranging pixel positions. The scheme introduces a random DNA operation to augment security, encoding the permuted images with a unique DNA technique and shuffling DNA bases using specialised DNA cubes. Performance analysis reveals that the decrypted medical images exhibit high visual fidelity, consistently achieving a PSNR above 35dB.
Nisha et al. have achieved secure ECG transmission with the Thing Speak platform of IoT with a triple DES algorithm for encryption and a water cycle optimisation algorithm for authentication. The authors have enabled Telecardiology in IoT-based clinical healthcare systems4849. have showcased a medical image encryption scheme designed to suit teleradiology applications in IoT platforms. The authors have employed a linear feedback shift register to generate pseudo-random numbers for shuffling pixel positions. Raspberry Pi B + processor is used to encrypt the medical images. Though these works display real-time implementation, the sensor data encryption, i.e., text encryption, is not reported. In addition, cloud storage and web page display are not included in these works47,49.
Inspired from the above literature review, this paper proposes a novel medical data and image encryption scheme using selective shuffling and inter & intra pixel diffusion. Wearable sensors are in contact with the human body and monitor the patient’s physiological parameters. The Raspberry Pi B + processor collects the patient’s health parameters, such as temperature pulse, using LM35 and pulse sensors. These sensor data and the patient’s medical image are encrypted using Python in a Raspberry Pi processor. The encrypted data is transmitted via the Thing Speak cloud and received by another Raspberry Pi at the receiver end to decrypt the cipher data. The flask webserver can view the decrypted data by the doctor at the other end.
The significant contributions of the proposed methodology are summarised as follows:
A novel medical image and text encryption scheme is proposed for a real-time IoT framework using three-level shuffling and two-level diffusion processes.
The novel selective shuffling increases the security by scattering the pixels randomly between the generated chaotic points.
Inter-Intra pixel diffusion based on the Combined Chaotic System (CCS) improves the resistance against statistical and differential attacks.
The encrypted patient’s health data and the medical image are transmitted via the ThingSpeak cloud environment to ensure secure transmission of E-healthcare data for real-time applications such as Telemedicine.
The rest of the paper is organised as follows. Section “Preliminaries” contains the preliminary information on CCS. A detailed illustration of the proposed methodology is presented in “Proposed methodology”. Section “Results and discussion” discusses the results and discussion of the proposed implementation, and “Conclusion” concludes the paper.
A Combined Chaotic System is developed by combining two one-dimensional chaotic maps in a single mechanism. Logistic and Tent maps are combined to develop a combined logistic-tent map. The mathematical expression of the combined logistic tent map is given in Eq. (1),
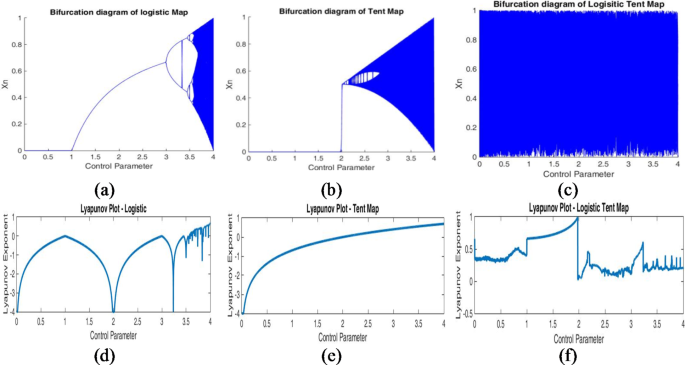
where, (:rho:) is the control parameter, and Z0 is the initial seed to maintain tent map in the chaotic range. The values of (:rho:) and Z0 are [2,4] and (0,1) respectively. The combination has increased the chaotic range from 0 to 4, as is evident from the bifurcation diagram in Fig. 1a–c. Figure 1c shows that the chaotic behaviour and the randomness of CCS are scattered over the entire surface of [0, 4]. Figure 1d–f represents the Lyapunov exponent plot of the logistic, tent and combined logistic-tent map. The Lyapunov plot of logistic and tent falls below the initial seed, i.e., 0. However, the Lyapunov exponent of the combined logistic-tent map is above the lower tail of the initial seed. This again proves the keys generated by the CCS possess extraordinary randomness.
Bifurcation and Lyapunov Plot: (a) Bifurcation diagram of logistic map, (b) Bifurcation diagram of tent map, (c) Bifurcation diagram of logistic-tent map, (d) Lyapunov exponent of logistic map, (e) Lyapunov exponent of tent map, (f) Lyapunov exponent of logistic-tent map.
The proposed work aims to securely transmit the patient’s medical data, namely the patient’s heartbeat, temperature and medical image, via Thing Speak cloud using a Wi-Fi module to the doctor’s web page. Raspberry Pi collects real-time health data from a pulse sensor and temperature sensor (LM35) to measure heartbeat in minutes, i.e., BPM (beats per minute) and the patient’s temperature. Along with the patient’s heartbeat and temperature, the patient’s diagnostic medical image is sent to the Raspberry Pi. The text and image encryption module in the Raspberry Pi (at the sender’s side) encrypts the patient’s sensitive data. Then, the encrypted medical image, pulse value and temperature are sent to the Thing Speak cloud. The Raspberry Pi from the user side (at the receiver’s side) collects the encrypted pulse, temperature value and medical image. Then, the decryption module in the Raspberry Pi receiver decrypts the pulse, temperature value, and medical image. The decrypted data is displayed on the webpage, which the doctor can view. The proposed IoT architecture for the secure transmission of patient’s sensitive data is portrayed in Fig. 2.
Proposed IoT framework for secure transmission of patient’s sensitive data.
The proposed medical image encryption module combines confusion and diffusion mechanisms. The confusion stage confuses the pixels of the medical image row-wise and column-wise based on the key sequences generated from the combined chaotic map. This is then followed by selective confusion of pixels between randomly selected two rows/ columns. The diffusion stage is responsible for changing pixel values in an image. In the proposed scheme, a two-level intra- and inter-pixel diffusion is done to break the statistical relationship exclusively between the adjacent pixels. A detailed illustration of the proposed medical image encryption scheme is shown in Fig. 3.
The steps involved in the proposed image encryption scheme are explained in detail as follows,
Step 1: Reading input image.
Input the DICOM image I of size M × N.
Step 2: Generating Key Sequence.
Feed the initial seed and control parameters {U1, U2, U3, X1, X2, X3, Y1, Y2, Y3} to the combined chaotic system. Let t, t1, t2 be the user-defined variables. Initially, iterate the chaotic system for t, t1 and t2 times to generate three sequences. Continue the iteration for M, N and M + N times after iterating the chaotic system for t, t1 and t2 times, respectively, to generate the chaotic sequences S1, S2, S3 and S4, respectively, as in the Eqs. (2–5),
Illustration of proposed medical image encryption scheme.
Step 3: Quantisation of key.
The chaotic key sequences S1, S2, S4 and S3 are quantised to be compatible with performing row, column and selective shuffling as in the Eqs. (6)–(9),
Step 4: Row and Column shuffling.
The quantised chaotic sequences Q1 and Q2 are obtained from the weighted matrix of chaotic sequences S1 and S2 respectively. For example, if S1= {0.45684782, 0.36378293, 0.94637284, 0.25648293, 0.85743628, 0.12746308, 0.32919194, 0.62451569}, then the weighted matrix of S1is S1’= {0.12746308, 0.25648293, 0.32919194, 0.36378293, 0.45684782, 0.62451569, 0.85743628, 0.94637284}. The quantisation unit maps the element’s position in the original and weighted chaotic sequences to obtain the quantised key, Q1= {6, 4, 7, 2, 1, 8, 5, 3}. Based on the elements of quantised key sequence Q1 and Q2, the pixels in the image IM×N are shuffled row-wise and column-wise, respectively.
Step 5: Selective Shuffling.
Selective shuffling is done by generating the cut-off points. Let the quantised key sequence be Q3= { λ1, λ2, …., λM}. Consider the consecutive elements of Q3 be λi and λi+1 representing the corresponding rows/columns. Four cut-off points C1, C2, C3 and C4 are determined from Q3 as in the Eqs. (10–13),
In selective shuffling, the row and column shuffled image pixels are again randomly between two rows. Not all the pixels between two rows/columns are shuffled, but the pixels between the determined cut-off points are swapped. The numerical example depicting selective shuffling is shown in Fig. 4. Consider, for example, (:{lambda:}_{i}=9,::{lambda:}_{i+1}=6).
In Fig. 4, consider Q3= {9, 6, 3, 8, 2, 5, 7, 4, 1}. Let us take the first two elements of Q3, 9 and 6. Now 9th and 6th rows are selected for shuffling and determine the four cut-off points from the Eqs. (12–15), {C1, C2, C3, C4} = {5, 3, 4, 7}. In the first stage, pixels from rows 9 and 6 are shuffled between C1 = 3 and C2 = 5. In the step 2, pixels between C3 = 4 and C4 = 7 are shuffled.
Step 6: Intra-Pixel Diffusion.
Feed the initial seed and control parameters U4, X4, Y4 to the combined chaotic system and iterate it for M× N× 4 times. Let S5 be the generated chaotic sequence, which is obtained as given in the Eqs. (14),
Quantise the generated chaotic sequence as per the Eqs. (15),
Selective shuffling process.
Intra-planar diffusion is done by mixing the pixel bits within itself based on the quantised chaotic sequence Q5. A detailed illustration of intra-planar diffusion is displayed in Fig. 5.
Figure 5 provides a detailed illustration of intra-planar diffusion with a numerical example. In the Fig. 5, a 5 × 5 image is considered. From the 5 × 5 image, let us consider a pixel 157, which lies in the 7th position with the index value (2, 2). The quantised chaotic key is grouped into four elements in each group, thus forming (M×N) groups comprising 4 elements each. Consider the binary value of the taken pixel i.e., binary value of 157 = 1001 1101. Group the binary value pairs as 10 01 11, and 01. Since the pixel 157 is present in the 7th position, key from G7 is taken to diffuse these pixel bits. As in the example, the binary bit pairs are diffused by mapping the pixel to the corresponding quantised key group to get the intra-pixel diffused image.
Numerical example of intra-planar diffusion.
Step 7: Inter-Pixel Diffusion.
Let the intra-pixel diffused image be (:{text{I}}_{text{d}(text{M}times:text{N})}^{{prime:}}). The hash of the intra-pixel diffused image is calculated using SHA-256. This hash is utilised to diffuse the inter pixels. Let the hash of (:{text{I}}_{text{d}(text{M}times:text{N})}^{{prime:}}) be hv. Quantise the 256-bit hash hv into (:{hv}_{1}^{{prime:}}) and (:{hv}_{2}^{{prime:}}) by the following Eqs. (16 and 17),
Inter-pixel diffusion is done by performing bitwise-exclusive OR operation between the hash and the current pixel to get the inter-pixel diffused pixel of the first row/column. Further, the chaining diffusion process is done by performing a bitwise XOR operation between the current and previous pixels of the intra-pixel diffused image to get the inter-pixel diffused image. The mathematical expressions of computing the inter-pixel diffused pixels are given below Eqs. (18)–(21),
The patient’s pulse and temperature data are encrypted by the text encryption module in the sender Raspberry Pi. Text encryption is performed as follows,
Step 1: Get the ASCII value of the character and convert it to binary.
Step 2: Perform the modulo-8 operation on the specific decimal character and left shift the character based on the result of the modulo operation.
This way of encrypting the text encrypts every character distinctly. This makes the adversary’s brute-force attack more tedious. The unique left-shifted character is converted to decimal to get the cipher text.
The proposed security framework for transmitting real-time patient data from remote clinics to specialised doctors is implemented by encryption and decryption algorithms on Raspberry Pi. Image and text encryption is scripted using the Python platform on the personal computer, with the system configuration of Intel core i5 with a 2.50 GHz clock speed CPU and a 64-bit Windows 10 operating system. The proposed work has considered 100 test DICOM images, out of which the results of 10 images are presented and discussed in this section. The DICOM images are downloaded from https://www.dicomlibrary.com/, https://www.osirix-viewer.com/resources/dicom-image-library/. This section also discusses the strength of the proposed encryption algorithm against various attacks, namely statistical, differential, key sensitivity and brute-force attacks. At the end of this section, the snapshots of patient’s sensitive data storage on the ThingSpeak cloud with its hardware implementation are presented.
This section discusses the efficiency and sternness of the proposed medical image encryption algorithm against various attacks. Figure 6 shows the three-sample test DICOM images and the corresponding images after row shuffling, column shuffling, selective shuffling and inter & intra- pixel diffusion processes. From Fig. 6, it can be viewed that the pixels of the images are effectively scrambled and diffused. Further, various tests with the corresponding numerical results are presented and tabulated in this section to demonstrate the effectiveness of the proposed algorithm.
Encryption test image results: (a) Test image 1, (b) Row-wise shuffled image 1, (c) Column-wise shuffled image 1, (d) Selective shuffled image 1, (e) final diffused image 1. (f) Test image 2, (g) Row-wise shuffled image 2, (h) Column-wise shuffled image 2, (i) Selective shuffled image 2, (j) final diffused image 2, (k) Test image 3, (l) Row-wise shuffled image 3, (m) Column-wise shuffled image 3, (n) Selective shuffled image 3, (o) final diffused image 3.
Statistical attack analysis helps to identify the statistical relationship between the neighbouring pixels of the image. A good encryption algorithm should be designed in such a way that it should break the statistical relationship between the adjacent pixels. This attack analysis is validated through several metrics such as information entropy, histogram analysis, chi-square test analysis, deviation from ideality test and correlation coefficient analysis.
Information entropy measures the degree of uncertainty/ randomness of the message. The mathematical formula for calculating entropy is given in the Eqs. (22),
P(i) represents the probability of the message occurrence. The message with higher entropy represents the higher randomness. The test image considered is 8-bit depth, so the cipher image entropy should be nearer to 8 to possess high randomness50,51. In addition to Global Shannon entropy, local entropy is useful in determining the true randomness of the cipher image. This can be done by determining the entropy of non-overlapping blocks. Table 1 displays the information entropy of the test images. Table 1 shows that the entropies of all the test images are nearer to 8, which means that the cipher images are entirely random. This proves the robustness of the encryption algorithm against statistical attacks.
Image histogram presents the visual representation of the statistical distribution of intensity levels of the image. The original and cipher image histograms should be completely different. The histogram of the cipher image should be flat. This means the cipher image should have all the intensity levels from 0 to 255 equally distributed. Figure 7 shows the histogram of the original and the cipher images. Figure 7 shows that the pixel values of the cipher images are equally distributed and the cipher image histograms are nearly flat, which are different in shape from the original image histograms. This flat and uniformly distributed histogram proves that a statistical attack by the adversary is impossible.
Histogram analysis. (a) Histogram of test image 1, (b) Histogram of Cipher image 1, (c) Histogram of Test Image 2, (d) Histogram of Cipher image 2, (e) Histogram of Test Image 3, (f) Histogram of Cipher image 3.
Chi-square analysis measures the statistical deviation of uniform distribution of the intensity levels among the image pixels. This can be calculated using the formula as in the Eqs. (23),
where, Kobserved is the observed number of pixels in each intensity level, Kexpected is the expected pixels in each intensity level. For 256 × 256 8 bit-depth image, Kexpected should be (:frac{256:times:256}{256}) = 256. The degree of freedom in evaluating the chi-square value is 255. The optimal chi-square value for 5% probability lies in 218.12–293.24. The chi-square values of the test images are tabulated in Table 2. Table 2 shows that the chi-square values are optimal and have passed the critical range test. Thus, the uniform distribution of intensity levels among the pixels has been validated statistically.
Deviation from ideality (DI) measures the deviation of the obtained histogram from the ideal histogram. The mathematical expression to calculate deviation from ideality is given in the Eq. (24).
H(ci) is the ideal cipher image histogram, H(c) is the obtained histogram. H(ci) =(:frac{256:times:256}{256}) = 256 for 8-bit depth image. The DI value should be nearer than zero for a perfectly encrypted image. Table 3 shows that the DI values of the test images are closer to zero, which means that deviation is very less and the obtained cipher image is closer to the ideal cipher image.
The correlation coefficient is the numerical measure of correlation between the adjacent pixels. The pixels of the original image are highly correlated in all three directions: horizontal, vertical, and diagonal. The cipher image should have zero correlation between the neighbouring pixels in all directions to break the statistical relationship between the pixels. The optimal correlation coefficient value for the cipher image should be between − 1 and 1, i.e., nearer to zero. The mathematical formulae for calculating the correlation coefficient are given in the Eqs. (25–28),
Table 4 shows the correlation coefficient values of the original and the cipher images. Table 4 shows that the correlation coefficient values of cipher images are nearer to zero, which means that the statistical relationship between the neighbouring pixels is completely broken. Figure 8 shows the pixel correlation of the original and the cipher images in horizontal, vertical, and diagonal directions. The correlation plot of the original plain image is linear and highly concentrated. The correlation plot of the cipher image is scattered across the entire surface. This again proves the robustness of the encryption algorithm against statistical attacks.
Correlation scattering plot analysis: (a) Horizontal correlation of test image 1, (b) Horizontal correlation of cipher image 1, (c) Vertical correlation of test image 1, (d) Vertical correlation of cipher image 1, (e) Diagonal correlation of test image 1, (f) Diagonal correlation of cipher image 1.
A good image encryption algorithm should generate perfectly random cipher pixels. The randomness of the generated cipher bits can be evaluated using the NIST SP-800-22 statistical test suite. NIST SP-800-22 test suite is a publication from the National Institute of Standards and Technology (NIST) that provides a set of statistical tests to assess the statistical properties of generated bit sequences, such as uniformity, independency and unpredictability. The p-values of all the tests should be at least 0.01 to pass the randomness tests successfully. p-values of NIST tests on the sample cipher bit streams generated by the proposed algorithm is given in Table 5. From Table 5, it can be inferred that the p-values of all the tests are greater than 0.01, which proves the randomness of the encrypted cipher bits.
This analysis is done to verify the robustness of the encryption algorithm for single-bit change in the plain image. This analysis considers two cipher images. C1(i, j) represents the cipher image from the plain image P1(i, j). C2(i, j) represents the cipher image from the plain image P2(i, j), which is constructed by changing a single pixel of P1(i, j). Differential attack analysis is done by measuring Number of Pixel Change Rate (NPCR) and Unified Average Change in Intensity (UACI) values between C1(i, j) and C2(i, j). NPCR and UACI values are calculated based on the formulae in the Eqs. (29–31),
The NPCR and UACI values are tabulated in Tables 6 and 7. The results show that NPCR and UACI values have passed the critical values tests52. Thus, the algorithm has a stronger ability to perform a resilient differential attack.
In this analysis, the full white or full black image is chosen. The cipher image of the full white and full black image is studied and analysed, as shown in Fig. 9. The security analysis metrics such as entropy, horizontal correlation, vertical correlation, diagonal correlation, and NPCR are calculated and tabulated in Table 8. From Fig. 9, the histogram of the cipher image is uniformly flat, and the tabulated values of security metrics are in the optimal range to prove the algorithm’s efficacy towards chosen/known plain text attack.
Chosen plain text attack analysis: (a) Full black image, (b) encrypted black image, (c) Histogram of (b), (d) Full white image, (e) encrypted white image, (f) Histogram of (e).
Key plays a crucial role in measuring the strength of the cryptosystem52,53,54,55,56,57,58. The cryptosystem should be highly sensitive to slight changes in the key. Figure 10 shows the key sensitivity analysis of the proposed cryptosystem. Figure 10 (b-e) represents the deciphered image for the single-bit change in the correct key set. The wrong key sets are,
Wrong key 1 K1’ = {U1 = 0.566788288829249, X1 = 3.784637253467822, Y1 = 2.567947345678932}, Wrong Key2 K2’= {U2 = 0.345682673354446, X2 = 3.826788334562379, Y2 = 3.456293225876541}, Wrong Key K3’={ U3 = 0.926347884782248, X3 = 3.764539257726522, Y3 = 3.546282763545873}, Wrong Key K4’= {U4 = 0.325587342457635, X4 = 3.863263543556856, Y4 = 2.576352854432521}. Figure 10 (f) represents the deciphered image with the correct key set. Figure 10 shows that the algorithm cannot decipher the correct image even for the single bit change in the key. This proves the sensitivity of key change for the proposed cryptosystem.
Key sensitivity analysis: (a) Original Image, (b) Deciphered Image with wrong key set K1’, (c) Deciphered Image with wrong key set K2’, (d) Deciphered Image with wrong key set K3’, (e) Deciphered Image with wrong key set K4’, (f) Deciphered Image with Correct key set.
The strength of the encryption algorithm lies in the strength of the key58. A good encryption algorithm should have substantial key space to defend against a Brute-force attack. To be stringent against the Brute-force attack, the algorithm’s key space should be greater than 2128. The key space of the proposed encryption algorithm is 2856 as given in Table 9. The key space is greater than 2128 to resist the exhaustive search attack.
A cropping attack analysis is carried out to analyse the efficiency of the proposed encryption algorithm against intentional/unintentional data loss. In this analysis, the part of the cipher image is intentionally cropped, and the cropped cipher image is sent to the decryption module to retrieve the deciphered image. Cropping attack analysis is carried out for 10% (81 × 81), 30% (140 × 140), 50% (181 × 181), 64 × 64, 32 × 32 data loss as shown in Fig. 11. From Fig. 11, it can be seen that the decryption algorithm can get back the meaningful decrypted image with several data losses.
Cropping attack analysis: (a) 10% cropped cipher image (81 × 81), (b) 30% cropped cipher image (140 × 140), (c) 50% cropped cipher image (181 × 181), (d) Cropped cipher image of size 64 × 64, (e) Cropped cipher image 32 × 32, (f) Deciphered image of (a), (g) Deciphered image of (b), (h) Deciphered image of (c), (i) Deciphered image of (d), (j) Deciphered image of (e).
Peak signal to noise ratio (PSNR) is a widely used metric for assessing the quality of an image. It measures the difference between original and the cipher image to measure the distortion or degradation of the image after decryption. It is calculated between the original image, and the deciphered image. PSNR is calculated mathematically as in Eq. (32).
where, (:{I}_{max}:)is the maximum possible pixel value of the image (e.g., 255 for 8-bit images) and MSE (Mean Squared Error) is calculated as in Eqs. (33),
where, (:I:left(i,jright)) is the pixel value of the original image, (:K:(i,j)) is the pixel value of the cipher image and (:mtimes:n:)is the dimensions of the images. The PSNR values are tabulated in Table 10. This proves the robustness of the proposed algorithm against data losses.
To test the algorithm’s efficacy against noise attacks, the cipher image is subjected to salt and pepper noise of various intensity levels. Salt and pepper noise is applied to the cipher image with varying intensity levels, such as 2%, 3%, 5%, 10% and 25%. The corresponding deciphered images are analysed, as shown in Fig. 12. The PSNR values of the original and the deciphered images from the noise-affected cipher images are calculated and tabulated in Table 11. This shows the robustness of the encryption algorithm against noise attacks.
Salt and pepper noise attack analysis: (a) Encrypted image with 2% noise, (b) Encrypted image with 3% noise, (c) Encrypted image with 5% noise, (d) Encrypted Image with 10% noise, (e) Encrypted Image with 25% noise, (f) Deciphered Image of (a), (g) Deciphered Image of (b), (h) Deciphered image of (c), (i) Deciphered image of (d), (j) Deciphered image of (e).
Complexity analysis is a crucial component of performance analysis used with encryption quality analysis to examine the effectiveness of suggested algorithms for real-time applications. An algorithm should possess less complexity and be resistant to a variety of attacks. The most crucial indicator of complexity is the encryption algorithm’s speed. If the cryptosystem takes less time to complete the encryption process (high-speed), then the algorithm is more suitable for resource-constrained IoT applications.
The proposed encryption algorithm performs three shuffling levels with two diffusion levels. Row-shuffling is done by generating M key sequences with M permutations. Column shuffling is carried out with N permutations. Selective shuffling is done in row-wise selective shuffling and column-wise selective shuffling. Four cut-off points are calculated in row-wise selective shuffling between C1 & C2 and C3 & C4. So, the total number of permutations in row-wise shuffling is 2 M. This is the same for column-wise selective shuffling. The number of permutations for column-wise selective shuffling is 2 N. Thus, the total number of permutation operations performed is fp = M + N + 2 M + 2 N = 3 M + 3 N = 3(M + N).
Two-level diffusion includes intra-pixel diffusion and inter-pixel diffusion. Intra-pixel diffusion requires M × N × 4 key generation and 4 level bit scrambling in each pixel. So, the number of diffusion operations in intra-pixel diffusion is M × N × 4. Inter-pixel diffusion requires M × N bit XOR operations. So, the total number of diffusion operations performed is fd= (M × N × 4) + (M × N) = 5 (M × N). Total key generation operations are fk = M + N + M + N +( M × N × 4) = 2(M + N) + (M × N × 4). Hence, the total complexity of the proposed encryption algorithm is f = fp + fd + fk = 3(M + N) + 5(M × N) + 2(M + N) + (M × N × 4) = 5(M + N) + 9(M × N). According to the Big-O notation principle, the overall complexity of the developed cryptosystem is O{5(M + N) + 9(M × N)}.
The time taken for encrypting the size 256 × 256 image on Raspberry Pi 3 B + is 0.038 s. Hence, the throughput of the proposed algorithm is 1.724 MB/s. The proposed work’s speed performance is significantly superior to that of Trujillo et al., Garcia et al., Kurunandan et al., and Bhagya et al.44,53,54,55, Fig. 13 depicts the speed performance analysis with the existing works. Table 12 gives the power consumption of the proposed encryption and decryption algorithm. The short duration of high CPU usage minimises the overall energy impact, consuming only a fraction of a watt-hour. The average power consumed for encrypting 256 × 256 images with 0.038 s is 2.8 W.
Encryption speed analysis.
The proposed medical image encryption algorithm is compared with the state-of-the-art methods in terms of entropy, NPCR, UACI, Vertical Correlation (VC), Horizontal Correlation (HC), Diagonal Correlation (DC) and key space as shown in Table 13. A comparison is also made for real-time cloud storage and transmission of patients’ sensitive data and text encryption.
In many related works, the report on real-time implementation of secure EHR transmission for IoT environments is not reported. Most works failed to perform real-time testing on hardware and cloud environments24,31,32,38,40,43,56,57,58. John et al.49 have done the real-time EHR transmission for the IoT environment with Raspberry Pi and Cloud. Still, the authors failed to report text encryption, and the UACI and correlation coefficient values are unsatisfactory, as reported in Table 13. This shows that the proposed cryptosystem is better than the available works reported in the literature.
The main purpose of designing secure health data transmission is to protect the patient’s medical images, temperature, and heartbeat values from unauthorised access. Raspberry Pi 3 B + has a quad-core Broadcom BCM2837B0 processor clocked at 1.4 GHz, significantly improving over the 1.2 GHz clock speed of the Raspberry Pi 3. It also features 1 GB of LPDDR2 RAM, which is more than enough for running most applications. Raspberry Pi 3 B + is programmed using Python, and it is an excellent single-board computer that offers improved performance, connectivity, and compatibility compared to its predecessor. Its versatility and affordability make it an ideal platform for various applications, including Telemedicine. Its GPIO (General Purpose Input/Output) pins make connecting to sensors, cameras, and other hardware components easy, making it an ideal platform for DIY projects. Figure 14 shows the hardware-implemented board. It consists of a Raspberry pi3 board, breadboard, LM35 Temperature sensor, Pulse sensor and ADS1115 Analog-To-Digital converter.
Snapshot of Hardware Implementation.
Thing Speak is a powerful IoT platform that provides users with a flexible and easy-to-use interface to collect, analyse, and visualise data from sensors and devices in real-time. Its open-source nature and API make it easy for developers to connect their devices to the Internet and send data to Thing Speak. Figure 15 shows the binary data achieved after the shuffling process (encryption) using CCS displayed in the Thing speak.
Temperature and pulse data storage in ThingSpeak cloud environment.
Figure 16 shows the decrypted form of temperature, pulse, and medical image received using the Raspberry pi 3 P+. It is displayed on the Flask web server so the doctor can view it from the receiver’s side. This helps the doctor monitor patients’ health in real-time wherever they are.
Patient data (Medical image, temperature data & pulse data) on the doctor’s web page.
A medical image and text encryption scheme has been developed to preserve the security and privacy of patients’ sensitive data. The developed system has collected patient’s health parameters using sensors deployed in remote healthcare locations. The patient’s health data and the corresponding medical image are collected and encrypted in a Raspberry Pi 3 B + processor. The multi-level encryption algorithm is based on selective shuffling and inter-intra-pixel diffusion. CCS triggers the shuffling and diffusion units by generating highly random key sequences. The larger key space of 2856 is achieved to resist brute-force attacks. The selective shuffling has efficiently scrambled the highly redundant medical image to combat differential attacks. The inter-intra-pixel diffusion process has efficiently broken the statistical relationship between the pixels to combat statistical attacks. The hash of the intra-pixel diffused image is used as the initial seed to diffuse the pixels in the next process. This has increased the resistance towards chosen plain-text and cipher-text attacks. The perfectly encrypted data is transmitted via the Thing Speak cloud and received by another Raspberry Pi at the receiver to decrypt the cipher data. The flask webserver can view the decrypted data by the doctor at the other end. The real-time storage on the Thingspeak cloud and the doctor’s web page data view are also presented. The developed implementation is tested and proven effective in preserving patients’ sensitive health information in an IoT environment.
Medical IoT systems often rely on wireless networks for communication between devices, patients, and healthcare providers. These networks are inherently vulnerable to interception, eavesdropping, and unauthorised access. Robust encryption protocols, authentication mechanisms, and secure communication standards must be employed to safeguard data transmitted over wireless channels. Additionally, securing communication in low-power or constrained devices, such as wearable medical devices, presents unique challenges. Medical IoT devices generate vast amounts of data, including patient monitoring information, diagnostic imaging, and real-time health metrics. Implementing security measures, such as encryption and access controls, can be resource-intensive for this data at scale. Ensuring ultra-low latency and real-time performance while processing and securing such data requires advanced computational and storage solutions.
Implementing the security algorithms on reconfigurable processors such as Field Programmable Gate Arrays (FPGAs) may help achieve low-latency security solutions.
Larger healthcare systems require encryption algorithms that balance security with efficiency. The algorithm should support device capability and computational cost for better scalability. The encryption and decryption process speed should be high without compromising security. For large-scale healthcare systems, specialised hardware, such as Graphics Processing Units (GPUs) or dedicated cryptographic processors, can accelerate medical image encryption across many devices. This approach ensures that image encryption processes do not delay critical functions, such as real-time monitoring and diagnosis.
All data generated or analysed during this study are included in this published article. The DICOM images are downloaded from https://www.dicomlibrary.com/;https://www.osirix-viewer.com/resources/dicom-image-library/.
Al-Ghaili, A. M. et al. A review on role of Image Processing techniques to Enhancing Security of IoT Applications. IEEE Access. 11, 101924–101948 (2023).
Article MATH Google Scholar
Das, S. & Mukhopadhyay, A. Security and privacy challenges in Telemedicine. CSI Commun. 20–23 (2011).
Garg, V. & Brewer, J. Telemedicine security: a systematic review. J. Diabetes Sci. Technol. 5, 768–777 (2011).
Article PubMed PubMed Central MATH Google Scholar
Zaidan, B. B., Zaidan, A. A. & Mat Kiah, M. L. Impact of data privacy and confidentiality on developing Telemedicine applications: a review participates Opinion and Expert concerns. Int. J. Pharmacol. 7, 382–387 (2011).
Article MATH Google Scholar
Liu, Y. Build an audit Framework for data privacy Protection in Cloud Environment. Procedia Comput. Sci. 247, 166–175 (2024).
Article MATH Google Scholar
Zandesh, Z. & Privacy Security, and Legal issues in the Health Cloud: structured review for Taxonomy Development. JMIR Form. Res. 8, (2024).
Belal, M. M. & Sundaram, D. M. Comprehensive review on intelligent security defences in cloud: taxonomy, security issues, ML/DL techniques, challenges and future trends. J. King Saud Univ. – Comput. Inf. Sci. 34, 9102–9131 (2022).
MATH Google Scholar
Alluhaidan, A. S. D. & Prabu, P. End-to-end encryption in resource-constrained IoT device. IEEE Access. 11, 70040–70051 (2023).
Article MATH Google Scholar
Olukoya, O. Assessing frameworks for eliciting privacy & security requirements from laws and regulations. Comput. Secur. 117, 102697 (2022).
Article MATH Google Scholar
Shah, W. F. Preserving privacy and security: a comparative study of Health Data regulations – GDPR vs. HIPAA. Int. J. Res. Appl. Sci. Eng. Technol. 11, 2189–2199 (2023).
Article MATH Google Scholar
El Assad, S. & Farajallah, M. A new chaos-based image encryption system. Signal. Process. Image Commun. 41, 144–157 (2016).
Article MATH Google Scholar
Ravichandran, D., Praveenkumar, P., Rayappan, J. B. B. & Amirtharajan, R. DNA Chaos Blend to secure medical privacy. IEEE Trans. Nanobiosci. 16, 850–858 (2017).
Article MATH Google Scholar
Zhang, S., Gao, T. & Gao, L. A novel encryption frame for medical image with watermark based on hyperchaotic system. Math. Probl. Eng. (2014).
Ravichandran, D., Rajagopalan, S., Upadhyay, H. N., Rayappan, J. B. B. & Amirtharajan, R. Encrypted biography of Biomedical Image – a Pentalayer Cryptosystem on FPGA. J. Signal. Process. Syst. https://doi.org/10.1007/s11265-018-1337-z (2018).
Article Google Scholar
Rajagopalan, S., Janakiraman, S. & Rengarajan, A. Medical image encryption: Microcontroller and FPGA Perspective. Med. Data Secur. Bioengineers. 278–304. https://doi.org/10.4018/978-1-5225-7952-6.ch014 (2019).
Abdelhaleem, S. H., Radwan, A. G. & Abd-El-Hafiz, S. K. Utilising LFSR and Feistel networks in image encryption. In Proceedings of the IEEE International Conference on Electronics, Circuits, and Systems 601–604 (Institute of Electrical and Electronics Engineers Inc., 2013). https://doi.org/10.1109/ICECS.2013.6815486.
Rajagopalan, S. & Upadhyay, H. N. Networked hardware assisted key image and chaotic attractors for secure RGB image communication. Multimed Tools Appl. (2018).
Rajagopalan, S., Upadhyay, R. S., Rayappan, H. N., Amirtharajan, R. & J. B. B. & ONChip peripherals are ON for chaos – an image fused encryption. Microprocess Microsyst. 61, 257–278 (2018).
Article MATH Google Scholar
Sasikaladevi, N., Geetha, K. & Sriharshini, K. Durga Aruna, M. RADIANT – hybrid multilayered chaotic image encryption system for color images. Multimed Tools Appl. https://doi.org/10.1007/s11042-018-6711-0 (2018).
Article Google Scholar
Praveenkumar, P. et al. Transreceiving of encrypted medical image — a cognitive approach. Multimed Tools Appl. https://doi.org/10.1007/s11042-017-4741-7 (2017).
Article MATH Google Scholar
Zhou, Y., Hua, Z., Pun, C. & Chen, C. L. P. Cascade Chaotic System with applications. IEEE Trans. Cybern. 45, 2001–2012 (2015).
Article PubMed MATH Google Scholar
Ravichandran, D. et al. DNA and Chaos Based Confusion-Diffusion for Color Image Security. In Proceedings – International Conference on Vision Towards Emerging Trends in Communication and Networking, ViTECoN 2019. https://doi.org/10.1109/ViTECoN.2019.8899483 (2019).
Diaconu, A. V. Circular inter-intra pixels bit-level permutation and chaos-based image encryption. Inf. Sci. (Ny) 355–356, 314–327 (2016).
Zourmba, K. et al. Fractional order 1D memristive time-delay chaotic system with application to image encryption and FPGA implementation. Math. Comput. Simul. 227, 58–84 (2025).
Article MathSciNet MATH Google Scholar
Wang, Q., Chen, X., Wei, M. & Miao, Z. Simultaneous encryption and compression of medical images based on optimised tensor compressed sensing with 3D Lorenz. Biomed. Eng. Online. 15, 118 (2016).
Article PubMed PubMed Central MATH Google Scholar
Wang, L. et al. Compressive sensing of medical images with confidentially homomorphic aggregations. IEEE Internet Things J. 6, 1402–1409 (2019).
Article MATH Google Scholar
Ramalingam, B., Rengarajan, A. & Rayappan, J. B. B. Hybrid image crypto system for secure image communication– A VLSI approach. Microprocess Microsyst. 50, 1–13 (2017).
Article MATH Google Scholar
Dhivya, R., Padmapriya, V., Sundararaman, R. & Rayappan, J. B. B. Amirtharajan. Chaos assisted variable bit steganography in transform domain. Electron. Lett. 54 (2), 1332–1334 (2018).
Article ADS MATH Google Scholar
Meng, F. Q. & Wu, G. A color image encryption and decryption scheme based on extended DNA coding and fractional-order 5D hyper-chaotic system. Expert Syst. Appl. 254, 124413 (2024).
Article MATH Google Scholar
Zahedian Nezhad, M., Bojnordi, A. J. J., Mehraeen, M., Bagheri, R. & Rezazadeh, J. Securing the future of IoT-healthcare systems: a meta-synthesis of mandatory security requirements. Int. J. Med. Inf. 185, 105379 (2024).
Article Google Scholar
Dash, S., Padhy, S., Anjali Devi, S., Sachi, S. & Patro, K. A. K. An efficient Intra-inter pixel encryption scheme to secure healthcare images for an IoT environment. Expert Syst. Appl. 231, 120622 (2023).
Article Google Scholar
Trujillo-Toledo, D. A. et al. Real-time medical image encryption for H-IoT applications using improved sequences from chaotic maps. Integration 90, 131–145 (2023).
Article Google Scholar
Nadhan, A. S. & Jeena Jacob, I. Enhancing healthcare security in the digital era: safeguarding medical images with lightweight cryptographic techniques in IoT healthcare applications. Biomed. Signal. Process. Control. 88, 105511 (2024).
Article Google Scholar
Das, S. & Namasudra, S. A. Novel hybrid encryption method to Secure Healthcare data in IoT-enabled Healthcare infrastructure. Comput. Electr. Eng. 101, 107991 (2022).
Article MATH Google Scholar
Kumari, S., Singh, M., Singh, R. & Tewari, H. A post-quantum lattice based lightweight authentication and code-based hybrid encryption scheme for IoT devices. Comput. Networks. 217, 109327 (2022).
Article MATH Google Scholar
Patil, K. S., Mandal, I. & Rangaswamy, C. Hybrid and adaptive cryptographic-based secure authentication approach in IoT based applications using hybrid encryption. Pervasive Mob. Comput. 82, 101552 (2022).
Article MATH Google Scholar
Dwivedi, A. D. & Srivastava, G. Security analysis of lightweight IoT encryption algorithms: SIMON and SIMECK. Internet Things (Netherlands). 21, 100677 (2023).
Article MATH Google Scholar
Rehman, M. U., Shafique, A. & Usman, A. B. Securing Medical Information Transmission between IoT devices: an innovative hybrid encryption Scheme based on Quantum Walk, DNA Encoding, and Chaos. Internet Things (Netherlands). 24, 100891 (2023).
Article MATH Google Scholar
Ravichandran, D., Padmaa, M., Rajagopal, N., Thanikaiselvan, V. & Amirtharajan, R. Chaos and DNA blended hybrid encryption algorithm for Secure Image transmission over DCT pre-coded OFDM. Wirel. Pers. Commun. 129, 703–727 (2023).
Article Google Scholar
Ravichandran, D. et al. An efficient medical image encryption using hybrid DNA computing and chaos in transform domain. Med. Biol. Eng. Comput. 59, 589–605 (2021).
Article PubMed MATH Google Scholar
Clemente-López, D. & Munoz-Pacheco, J. M. De Jesus Rangel-Magdaleno, J. Experimental validation of IoT image encryption scheme based on a 5-D fractional hyperchaotic system and Numba JIT compiler. Internet Things. 25, 101116 (2024).
Article Google Scholar
Khan, M. S. et al. A Novel Cosine-modulated-polynomial chaotic map to strengthen image encryption algorithms in IoT environments. Proc. Comput. Sci. 246, 4214–4223 (2024).
Article MATH Google Scholar
Lai, Q. & Hua, H. Secure medical image encryption scheme for Healthcare IoT using novel hyperchaotic map and DNA cubes. Expert Syst. Appl. 264, 125854 (2025).
Article MATH Google Scholar
Jain, K. et al. A lightweight multi-chaos-based image encryption Scheme for IoT Networks. IEEE Access. 12, 62118–62148 (2024).
Article MATH Google Scholar
Gu, Z. et al. IEPSBP: a cost-efficient image encryption Algorithm based on parallel chaotic system for Green IoT. IEEE Trans. Green. Commun. Netw. 6, 89–106 (2022).
Article MATH Google Scholar
Elhoseny, M. et al. Secure Medical Data Transmission Model for IoT-Based Healthcare systems. IEEE Access. 6, 20596–20608 (2018).
Article Google Scholar
D., M. & B., M. Image encryption using modified perfect shuffle-based bit level permutation and learning with errors based diffusion for IoT devices. Comput. Electr. Eng. 100, 107954 (2022).
Article MATH Google Scholar
Raheja, N. & Kumar Manocha, A. IoT based ECG monitoring system with encryption and authentication in secure data transmission for clinical health care approach. Biomed. Signal. Process. Control. 74, 103481 (2022).
Article MATH Google Scholar
John, S. & Kumar, S. N. IoT based medical image encryption using linear feedback shift register – towards ensuring security for teleradiology applications. Meas. Sens. 25, 100676 (2023).
Article Google Scholar
Wu, Y. et al. Local Shannon Entropy measure with statistical tests for image randomness. Inf. Sci. (Ny). 222, 323–342 (2013).
Article MathSciNet MATH Google Scholar
Anwar, S. & Srivastava, A. A threefold chaotic image encryption technique for efficacious image data protection. Int. J. Comput. Appl. 0, 1–9 (2024).
MATH Google Scholar
Wu, Y., Member, S., Noonan, J. P. & Member, L. NPCR and UACI randomness tests for image encryption. Cyber J. Multidiscip. J. Sci. Technol. J. Sel. Areas Telecommun. 31–38 (2011).
Trujillo-Toledo, D. A. et al. Real-time RGB image encryption for IoT applications using enhanced sequences from chaotic maps. Chaos Solitons Fractals. 153, 111506 (2021).
Article MathSciNet MATH Google Scholar
García-Guerrero, E. E., Inzunza-González, E., López-Bonilla, O. R., Cárdenas-Valdez, J. R. & Tlelo-Cuautle, E. Randomness improvement of chaotic maps for image encryption in a wireless communication scheme using PIC-microcontroller via Zigbee channels. Chaos Solitons Fractals. 133, 109646 (2020).
Article MathSciNet MATH Google Scholar
Umamakeswari, A. Hardware implementat ion of secure image transmission in raspberry PI. Int. J. Mech. Eng. Technol. 9, 670–678 (2018).
MATH Google Scholar
Guesmi, R., Farah, M. A. & Ben A new efficient medical image cipher based on hybrid chaotic map and DNA code. Multimed Tools Appl. 80, 1925–1944 (2021).
Article MATH Google Scholar
Vijaya Bhaskara Rao, B., Rawat, U., Roy, S. & Lal, C. S. O. R. C. H. I. C. A hybrid image Cipher for IoT Applications using second Order Reversible Cellular Automata. IEEE Access. 12, 146147–146159 (2024).
Article MATH Google Scholar
Alharbi, A. R. et al. Enhancing internet of things communications: development of a new S-box and multi-layer encryption framework. J. King Saud University-Computer Inform. Sci., 102265. (2024).
Download references
Department of ECE, Mepco Schlenk Engineering College, Sivakasi, 626 005, India
Dhivya Ravichandran & W. Sylvia Lilly Jebarani
Faculty of Engineering, King Abdulaziz University, Jeddah, 22254, Kingdom of Saudi Arabia
Hemalatha Mahalingam
Department of Computer Sciences, Marquette University, Milwaukee, WI, 53233, USA
Padmapriya Velupillai Meikandan
School of Electrical and Electronics Engineering, SASTRA Deemed to be University, Thanjavur, 613 401, India
Padmapriya Pravinkumar & Rengarajan Amirtharajan
You can also search for this author in PubMed Google Scholar
You can also search for this author in PubMed Google Scholar
You can also search for this author in PubMed Google Scholar
You can also search for this author in PubMed Google Scholar
You can also search for this author in PubMed Google Scholar
You can also search for this author in PubMed Google Scholar
Dhivya Ravichandran, Sylvia Lilly Jebarani, Hemalatha Mahalingam and Padmapriya Velupillai Meikandan, designed the study, conducted the experiments, and analysed the data. Padmapriya Pravinkumar and Rengarajan Amirtharajan provided critical feedback, helped write and edit the manuscript, and guided the project. All authors reviewed and approved the final manuscript.
Correspondence to Dhivya Ravichandran.
The authors declare no competing interests.
All authors have read, understood, and have complied as applicable with the statement on “Ethical responsibilities of Authors” as found in the Instructions for Authors.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
Reprints and permissions
Ravichandran, D., Jebarani, W.S.L., Mahalingam, H. et al. An efficient medical data encryption scheme using selective shuffling and inter-intra pixel diffusion IoT-enabled secure E-healthcare framework. Sci Rep 15, 4143 (2025). https://doi.org/10.1038/s41598-025-85539-5
Download citation
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-025-85539-5
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Advertisement
© 2025 Springer Nature Limited
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.


More Stories
What Is Meaningful Connectivity?
Connect, Discuss, Inspire: Dive Deep with Special Interest Groups
Our Voices Are Making a Difference in the Fight for Strong Encryption