Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
Advertisement
Scientific Reports volume 15, Article number: 9831 (2025)
Metrics details
Internet of Things (IoT) denotes a system of interconnected devices equipped with processors, sensors, and actuators that capture and exchange meaningful data with other smart systems. IoT technology has been successfully applied across various sectors, including agriculture, supply chain management, education, healthcare, traffic control, and utility services. However, the diverse range of IoT nodes introduces significant security challenges. Common Internet of Things safety features like encryption, authentication, and access control frequently fall short of meeting their desired functions. In this paper, we present a novel perspective to IoT security by using a Graph-based (GB) algorithm to construct a graph that is evaluated with a graph-based learning Intrusion Detection System (IDS) incorporating a Graph Attention Network (GAT). In addition, we leveraged a small benchmark NSL-KDD dataset to conduct detailed performance evaluation of the GNN model by focusing on essential key metrics such as F1-score, recall, accuracy, and precision to guarantee comprehensive analysis. Our findings validate the effectiveness of the GNN-based IDS in detecting intrusions, which highlights its robustness and scalability in mitigating the evolving security challenges within IoT systems.
In today’s rapidly evolving world of IoT technologies, the rapid advancements of computers and network devices continue to improve to meet its increasing demands. However, protecting IoT devices remains an immediate and critical concern. In the field of cyber security, an intrusion refers to any attempt (unauthorized or malicious) to gain access, alter, or compromise the data, system or network. Intrusions can have many shapes and can be carried out by individuals or automated programs (malware), with malicious intent1. An intruders primary objective is to gain unauthorized access, disturb system functions, infiltrate sensitive data, or jeopardize the integrity and security of the system or network2. Detecting and preventing intrusions is a fundamental aspect of cyber security which is achieved through various security measures, including antivirus software, firewalls, security policies, intrusion detection systems, and intrusion prevention systems. These measures are designed to detect and mitigate intrusions, minimizing the damage and protecting the confidentiality, integrity and availability of the system3,4. Intrusion Detection System (IDS) is a tool used to perform deep inspection of packets to guard a network or a system from the malicious attempts performed by the intruders. During the inspection of the packets, the IDS will not examine header only but also data contained in the packet. IDS are automatic devices that actively monitors network traffic, performs analysis and detects the events of intrusions, illegitimate access occurring in the network or computer host and notifies the security administrator such events. The goal of IDS is to enhance the security mechanism of the network system and to guarantee the security services5. IDS can identify the intrusion using two common techniques: Signature based IDS and Anomaly-based IDS. SIDS detects the specific patterns by matching with known intrusions. Signature based intrusion or Rule based intrusion detection system searches for particular patterns or intrusions by matching the data with known intrusions to find intrusions. Signature based detection mechanism has low false alarms and good accuracy rate. Anomaly based intrusion detection system analyzes, detects and reports the unusual events or observations which do not conform to an expected or normal patterns in the dataset6. Based on the monitoring platform IDS can be commonly classified into two types: NIDS (Network-based IDS) and HIDS (Host-based IDS). NIDS are installed at the network’s entrance to monitor and analyze inbound and outbound data in order to detect malicious occurrences and shield the network from them. HIDS that resides or deployed on a single system to monitor and analyze internal activities of the host and identify which application tries to accesses what resource under which conditions and attempts illegitimate access. Despite these capabilities, the increasing sophistication of attack methods presents significant challenges for IDS. As a result, detecting previously unknown attack patterns remains a persistent weakness in current systems. Machine and deep learning have gained significant traction in various domains, including image processing, storage systems, and cybersecurity7. In cybersecurity, deep learning models like convolutional neural networks (CNN)8, multi-layer perceptron (MLP) are being incorporated into IDS to improve network detection capabilities9,10. These models are primarily trained to process tabular data formats like vectors or grids, which do not adequately capture the relationships or interdependences found in network flows11. NIDS based on learning algorithms typically treat flow data records independently, overlooking the relationships, dependences between traffic patterns which are crucial for intrusion detection12,13. This reduces their ability in detecting advanced IoT network attacks like botnets14, distributed port scans15, and DNS amplification attacks16, which demands a comprehensive global view of network traffic17. Internet of Things (IoT) traffic flows exhibits graph-like structure, making GNNs an ideal approach for analyzing graph data. GNNs are more adaptable and scalable solutions for dynamic IoT networks, enabling more precise attack detection compared to conventional methods18. GNNs utilize message-passing mechanism to iterate, aggregate information from the neighboring nodes to learn both structural and topological features of networks, increasing their capacity to detect possible attacks by preserving critical features about the relationships within the data. However, stability and reliability of GNN-based intrusion detection systems (IDS) have not yet reached the desired levels, primarily due to inefficient optimized training data19. To date, existing research on GNN models for IDS has primarily focused on representing flow data as either nodes or edges in a graph structure. Authors in20 represented network traffic flows as graph edges, with endpoints mapped to graph nodes. Another study in19 proposed a method where network flows are modeled as a graph, with each node containing flow features such as (IP source, IP destination, port, protocol, request, response) tuples. Similarly, authors in21 presented a heterogeneous graph model designed from network flows, where each flow is represented by three nodes: a source node, a flow node, and a destination node22. GNN-based learning model is proposed to address these limitations by examines traffic patterns and network flow with relationships to enhance the accuracy and detection of distributed IoT attacks. GNNs processes structured data, enables them to learn and capture complex interactions between connected devices, makes them particularly suitable for detecting communication patterns and spatial relationships that are crucial for anomaly and threat detection17. In this paper, we introduce a novel Graph-Based IDS leveraging Graph Attention Network (GAT) techniques. The system operates in four main stages: pre-processing, graph creation, model design/training and intrusion detection. The first and most fundamental step in our proposed system is data processing, often referred to as data engineering. During the Graph Creation stage, network traffic data is transformed into graph structures that capture the relationships between entities. Third step is defining the overall design and structure of a Graph Neural Network, which dictates how the model processes graph-structured data. In the Intrusion Detection stage, GNNs analyses the graph data to identify potential intrusions. This approach enhances detection accuracy by utilizing the rich contextual information inherent in graph representations.
Author in23 explored various datasets, NSL-KDD, CICIDS-2017, and IOTID20, to evaluate IDS performance under real-world attack scenarios. Hybrid models, such as Pearson-Correlation Coefficient (PCC), with deep learning architectures have demonstrated improved detection rates and reduced false alarms. However, further research is needed to address issues related to real-time processing, imbalanced datasets, and novel attack detection in IoT security. According to research24, detection accuracy increases and false alarms diminish as DL-based methods like neural networks and decision trees automatically learn attack patterns. Nevertheless, problems such as high computational costs, real-time application, and biased datasets remain crucial concerns in the development of IDS. Future progress should focus on improving resource-efficient models, integrating real-time detection, and enhancing dataset quality to develop strong and scalable IoT security solutions. Intrusion Detection Systems (IDS) are significantly important in cyber security, with models like Decision Trees, Random Forest, and XGBoost exhibiting strong performance25. Research underscore best performance of boosting models, especially XGBoost, over traditional classifiers in IoT attack detection, achieving greater precision and recall. However, future studies should center on handling dynamic IoT environments, optimizing real-time detection, and minimizing lateral movement threats to enhance network security. The swift growth of IoT in various sectors has prompted major security worries, making the need for smart intrusion detection systems (IDS)26. The results confirm that ensemble machine learning improves intrusion detection by utilizing model diversity to achieve greater accuracy. Future research should investigate hybrid feature selection methods to enhance detection efficiency in IoT security. Cyberattacks27 are an escalating threat, prompting organizations to seek advanced detection methods, with ML and DL showing promising results. However, flat data fails to capture attack behavior effectively, whereas graph structures offer a more accurate, resilient representation. This paper focuses on GNN, which have demonstrated success in learning attack patterns from graph-structured data for both network and host-based intrusion detection. Author reviewed latest research papers and datasets, highlighting the advantages of GNNs in improving detection accuracy. Furthermore, the paper discusses difficulties and proposes avenues for future research aimed at optimizing GNNs for use in cybersecurity. The complexity of network traffic28 has increased, leading in greater security risks and emphasizing the necessity for robust and effective IDS. Integration of Artificial Neural Networks (ANNs) has shown encouraging performance, achieving superior accuracy compared to other traditional methods. Future research aims to enhance the robustness of IDS by incorporating clustering algorithms with hybrid ML models enabling both dynamic and adaptive threat detection. Graph Neural Networks (GNNs)29 have gained prominence as a powerful technique for enhancing IDS due to their powerful ability to model complex relationships and analyze structural dependences within network data. Author underlines the difficulties encountered at every phase and delivers a methodical review of existing research. Despite the GNNs potential, challenges like user data privacy and model interpretability persist. Future studies in this field will focus to improve these aspects to bolster IDS and accommodate the adaptive threats posed by networks. Authors in30 explored the use of GNN in IDS and addressed issues associated with preprocessing of network data. An innovative approach is proposed in transforming network flow data into graph structured, nodes represent flow characteristics and edges depict connections between them. Experiments results indicate that the model attained a high level of accuracy: 94% on the CIC-IDS2017 dataset and 96.4% on the UNSW-NB15 dataset. Machine learning algorithms like SVM, RF, decision trees treat data points independently, limited to capture the interdependencies among packets, network flows, or attack patterns. Additionally, deep learning models like CNNs and LSTMs also suffers from the lack interpretability, making it difficult and complex to understand or explain their decision making. Graph-Based Clustering (GB) and Graph Neural Networks (GNNs) can effectively overcome several limitations of conventional models by leveraging the graph structure to capture their dependencies, relationships within the network data in detecting the intrusions. GB provides flexibility by clustering traffic based on similarity, enabling better generalization for detecting novel attack patterns30. When combined with Graph Attention Networks (GATs), it focuses on the most relevant parts of the graph, improving anomaly detection. Additionally, GATs enhance interpretability by assigning attention to key features, offering more transparency in decision-making, and aiding model refinement.
In machine learning, a dataset serves as the foundation for training, validating, and testing models. Since machine learning algorithms are inherently data-driven, they rely on datasets to generate functions/methods during the training process, which are then used to make predictions on unseen data. NSLKDD is well-structured updated version of KDD Cup 1999 dataset typically consists of 41 input features and corresponding output label31. This dataset has no redundant records, making it more acceptable for evaluating different intrusion detection systems fairly. The size of the training and testing sets is manageable, enabling researchers to conduct experiments without requiring excessive computational resources. The dataset outright labels that indicate whether a particular connection is normal or corresponds to a typical type of attack. Machine learning algorithms are frequently trained and validated using NSL-KDD dataset for the detection of intrusions. Researchers use NSL-KDD dataset to evaluate how well different algorithms perform in detecting various types of network attacks32. The small training NSL-KDD dataset consists of 1,011 records and with all 43 features, making it well suitable for evaluating the efficacy of IDS in detecting cyber-attacks. The smaller size of the small NSL-KDD training dataset makes it appropriate to train and test lightweight IDS models for IoT environments. The dataset comprises of different types of attacks which are relevant to IoT security. IoT devices and networks are often targeted by malicious actors using similar approaches33.
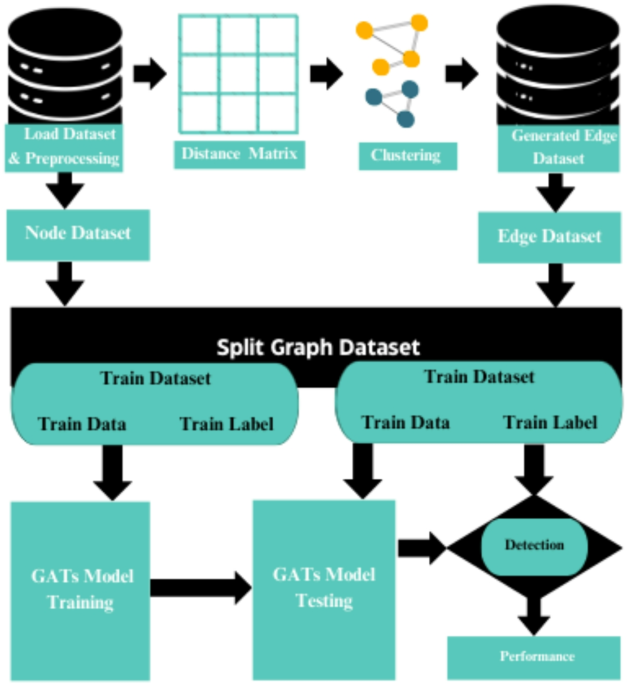
This section presents a structured architectural framework that emphasizes a systematic approach for developing and evaluating the proposed intrusion detection model based on Graph Attention Networks (GATs) through the generation of graph-structured data to enhance the detection accuracy. The architectural design of the proposed system is presented in Fig. 1. Following steps are used to design strong and efficient model through data preprocessing, graph construction, systematic model training, and intrusion detection/evaluation. The first and critical phase of the proposed system is data preprocessing, often referred to as data engineering. This phase is important as it ensures that the data is clean, relevant, and properly formatted before it is suitable for analysis.
Architectural design for the proposed system.
During the pre-processing of the NSL-KDD dataset, we applied two important techniques to prepared data for the model. One-hot encoding, to convert categorical features (Protocol Type, Service, and Flag) into binary vectors, enabling features to be used in algorithms that require numeric input. Min-Max scaler, to normalize all numerical features to a specific range, usually [0, 1]31. In the realm of data analysis and learning, understanding the relationships between samples is important. Distance metrics serve as a critical method for quantifying how alike or unalike samples are. The Euclidean distance is fundamental measure that identifies the shortest path or straight-line distance between points within a Euclidean space. The Euclidean distance is the important measures for accessing the similarity or dissimilarity between samples. The calculated Euclidean distances between rows of the dataset are stored in distance matrix I34. The similarity matrix generated is square and has dimensions that match the number of samples in the data set. If the data set has n samples (rows), the similarity matrix will be (n * n). Clustering refers to the process of categorizing items into useful subclasses, where members of the same cluster are identical to one another and members of different clusters are quite distinct. As a result, clustering methods can assist in the categorization of data for the detection of intrusions. The graph-based clustering algorithm is a commonly employed method for automatically partitioning a data set into multiple clusters34,35. Threshold is calculated based on maximum, minimum and cluster precision values of the distance matrix I. Consequently, if the weight of an element exceeds the calculated threshold, it is removed from the matrix I. Threshold is calculated based on maximum, minimum values of the distance matrix I. Consequently, if the weight of an element exceeds the calculated threshold, it is removed (set to 0) from the matrix I. The refined distance matrix I is used as adjacency matrix to create a graph clusters. Constructing a graph entails creating a network of nodes (or vertices) and edges (or connections) between them. Python libraries provide easy and user-friendly functions to create, manipulate, and analyze graphs36,37. For every element in the refined distance matrix I, create a corresponding node in the graph. Then iterate through the distance matrix to establish edges between node based on their distances. Each edge is to be assigned a weight that corresponds to its distance in the matrix. Before adding an edge, verify that it does not already exist to ensure each pair of nodes is connected only once. Annotate the edges with their corresponding weights to show the distances between the nodes. The next step is to construct the edge dataset representing the edges between the packets. Iterated through the graph to extract edge information. For each entry ‘(i, j)’ where ‘i is connected with j’. The edges are arranged in an organized format using a tabular structure. The generated edge dataset consists of 250,654 rows, where each row represents an edge with three columns: Source Node, Target Node, and Weight. The edge dataset defines the structure of the graph by specifying how nodes are connected. The attribute set provides additional details that describe the nodes, enriching the graph with more information that can be used in analysis14. Thus the combination of small NSL-KDD dataset and generated edge dataset are treated as graph dataset.
Graph data set is a powerful approach for modeling and analyzing complex systems where the relationship between entities are critical. Graph dataset contains of two main components: an edge dataset that defines the connections between nodes, and an attribute set that provides descriptive properties about the nodes. This framework facilitates deep insight via specialized algorithms, such as GNN19. After the graph data is constructed from NSL-KDD dataset, nodes representing row entities while edges depict similarity relationships. Flow attributes are encoded, normalized and serve as input for GAT model. A split of, 80–20 is applied, where 80% of the data samples are randomly selected for the training and 20% samples for the evaluating the performance of the model. The third step presents the overall architecture and framework of Graph Attention Network (GAT), explaining how the proposed model processes the graph-structured data to learn patterns. The architecture of the model comprises of several key elements and design choices that influence the model’s operation, learning process, and data generalization. The model is trained on 80% of the training data, incorporates a moderately deep architecture consisting 110 hidden units, two attention heads per layer, and two attention layers to enhance feature learning. All these elements work together to extract meaningful patterns from structured data, facilitating the efficient detection of intrusions. The training spans 500 epochs and employs a batch size of 16 to optimize model performance and balance computational efficiency. Each attention head computes attention coefficients for a specific subset to capture the importance of node relationships. These coefficients quantify the relative importance of connections between nodes, determine how much attention each node should focus to its neighbors19. The attention coefficients computed are used to assign weights to the input features of each node, to capture relevant relationships. This ensures node representation is strongly influenced by connections, allows the model to prioritize critical relationships. To optimize the model, Stochastic Gradient Descent (SGD) is applied with a learning rate of 0.01 and a momentum of 0.02 to ensuring efficient learning stable convergence. The output of the attention layers17 is produced by combining and transforming the weighted features, capturing the essential relationships within the graph. This transformation detects both local and global patterns in the graph, providing valuable insight about possible intrusions. The size of the output layer is determined dynamically according to the number of classes: it is 2 for binary classification and 4 for multi-class classification. The loss function used is sparse categorical cross-entropy, which efficiently processes integer-encoded class labels. The propose model is trained using labelled data, where nodes are classified as Normal, Probe, DoS, R2L, and U2R for multi-classification and normal/malicious for binary classification. During training, the model fine tunes its parameters to recognize differences between various classes or behaviors, effectively distinguishing malicious nodes in a network from normal ones. The training process is designed to reduce a loss function usually cross-entropy loss that measures the difference between predicted labels and actual labels and to identify relationships within the graph data. In final step model’s performance and its power to generalize to unseen data are evaluated. During the intrusion detection, 20% of the unseen or test data is used to identify potential intrusions. Proposed model significantly improves detection accuracy by effectively using rich contextual information contained in graph representations. Key performance indicators like accuracy, F1-score, precision, and recall are used to access the efficacy of the GAT model. Therefore, the proposed model improves the performance in detecting and predicting the intrusion within the IoT environment using created graph data.
The efficacy of the Graph Attention Network (GAT) in identifying different classes of network intrusions (DoS, Probe, R2L, U2R) as well as normal traffic is assessed using key essential metrics such as precision, recall, F1-score, and accuracy. In IoT security, all these metrics, ensure effective threat detection by balancing false positives and false negatives. A high-performing model must accurately detect attacks while minimizing unnecessary alerts to maintain system reliability3. The accuracy demonstrated how the model’s performance when evaluated on test data. The results demonstrate that the GAT performs well in detecting attack types, with high precision, recall, and F1-scores. However, the model might struggle more with rare and subtle attack types like U2R, where precision and recall are lower for multi classification. The GAT models exhibit outstanding overall accuracy, with 98% for binary classification and 99.20% for multi-class classification, respectively. Table 1 highlights the performance of GAT model for binary and multi class attack types.
The graphical visualization of findings in form of precision, recall, f1-score and confusion matrix is depicted in Figs. 2 and 3.
Performance of GAT classifier for binary and multi classification.
Confusion matrix for multi and binary classification.
The proposed method is evaluated against multiple state-of-the-art approaches from recent studies to assess its effectiveness, accuracy, and overall performance in comparison to existing solutions. The results demonstrate that the GAT model achieves superior performance, particularly in terms of accuracy, outperforming all other compared methods. GAT demonstrates strong potential for use in IoT intrusion detection, particularly for more frequent and distinguishable attack types. Among the approaches23, used a CART for binary classification, achieving 99% accuracy and an F1 score of 98%, though precision and recall of 99%. In contrast25, employed a XGBoost method, reaching 99% accuracy and 99% precision and recall. In study26, an ensemble method was employed, achieving 98% accuracy, and along with precision, F1 score, and recall of 98% each. The ANN model in28 achieved 97.50% accuracy, 95.70% F1 score, 99.00% precision, and 96.70% recall. Additionally29, used a GCN with an accuracy of 96.25%. Our proposed GAT based model stands out by offering high accuracy, better precision, and recall, which are essential for minimizing false negatives and false positives. Compared to the other learning techniques, our model excels in accuracy, F1 score, precision, and recall, providing a better and reliable defense against evolving network threats. Table 2 provides a detailed comparison of different intrusion detection methods, evaluating their effectiveness based on key parameters including accuracy, F1-score, precision, and recall.
At present, there are no graph-structured datasets for assessing the efficacy of graph neural networks in identifying intrusions within IoT environments. In order to fill this gap, we developed a Graph Attention Network (GAT) model that employs a novel graph-based clustering method to convert raw network data into a graph-structured format, with nodes and edges serving as efficient encodings of the information. In this framework, nodes thoroughly represent all characteristics of the network flows, and edges are formed by creating connections between packets according to their similarity distance. The proposed model is used to analyze the data from the constructed graph data and to pinpoint possible intrusions in the IoT system. The suggested method shows outstanding stability and performance, reaching an accuracy of 98% for binary classification and 99.20% for multi-class classification tasks. This allows us to use the advantages of graph neural networks for intrusion detection, even when no pre-existing graph data is available. The findings demonstrate that the graph-based learning approach is effective for enhancing intrusion detection systems. This therefore opens the door to new intelligent and robust network defense mechanisms for IoT environments. The findings of this study will play a crucial role in advancing IoT security, offer valuable insights and help to establish a robust base for future research, developments, and innovative security solutions.
The datasets generated during and/or analysed during the current study are not publicly available but are available from the corresponding author on reasonable request.
Khraisat, A. & Alazab, A. A critical review of intrusion detection systems in the internet of things: Techniques, deployment strategy, validation strategy, attacks, public datasets and challenges. Cybersecurity 4, 1–27 (2021).
Google Scholar
Deriba, F. G., Salau, A. O., Mohammed, S. H., Kassa, T. M. & Demilie, W. B. Development of a compressive framework using machine learning approaches for SQL injection attacks. Przeglad Elektrotechniczny. 7(1), 181–187. https://doi.org/10.15199/48.2022.07.30 (2022).
Article Google Scholar
Ahanger, A. S., Khan, S. M. & Masoodi, F. Building an intrusion detection system using supervised machine learning classifiers with feature selection. In Inventive Systems and Control: Proceedings of ICISC 2022 (pp. 811–821). (Springer, 2022).
Ngueajio, M. K., Washington, G., Rawat, D. B. & Ngueabou, Y. Intrusion detection systems using support vector machines on the kddcup’99 and nsl-kdd datasets: A comprehensive survey. In Proceedings of SAI Intelligent Systems Conference (pp. 609–629). (Springer, 2022).
Kannari, P. R., Chowdary, N. S. & Biradar, R. L. An anomaly-based intrusion detection system using recursive feature elimination technique for improved attack detection. Theor. Comput. Sci. 931, 56–64 (2022).
MathSciNet MATH Google Scholar
Salau, A. O., Assegie, T. A., Akindadelo, A. T. & Eneh, J. N. Evaluation of Bernoulli Naive Bayes model for detection of distributed denial of service attacks. Bull. Electr. Eng. Inf. 12(2), 1203–1208. https://doi.org/10.11591/eei.v12i2.4020 (2023).
Article Google Scholar
Bakhsh, S. et al. Enhancing IoT network security through deep learning-powered intrusion detection system. Internet Things. 24, 100936 (2023).
MATH Google Scholar
Yin, J. et al. Internet of things intrusion detection system based on convolutional neural network. Comput. Mater. Contin. 75, 2119–2135 (2023).
MATH Google Scholar
Sanju, P. Enhancing intrusion detection in IoT systems: A hybrid metaheuristics-deep learning approach with ensemble of recurrent neural networks. J. Eng. Res. 11(4), 356–361 (2023).
MATH Google Scholar
Farooq, M. A. N. S. O. O. R. Improved intrusion detection in the internet of things: A multi-Layered neural network approach and analysis. Int. J. Curr. Res. 23(2), 268–273 (2024).
MATH Google Scholar
Osa, E., Orukpe, P. E. & Iruansi, U. Design and implementation of a deep neural network approach for intrusion detection systems. e-Prime-Adv. Electr. Eng. Electron. Energy. 7, 100434 (2024).
MATH Google Scholar
Hidayat, I., Ali, M. Z. & Arshad Arshad. Machine learning-based intrusion detection system: An experimental comparison. J. Comput. Cogn. Eng. 2(2), 88–97 (2023).
MATH Google Scholar
Krishnamoorthy, G. & Sistla, S. M. K. Exploring machine learning intrusion detection: Addressing security and privacy challenges in IoT-A comprehensive review. J. Knowl. Learn. Sci. Technol. 2(2), 114–125 (2023).
Putra, M. A. R., Ahmad, T. & Hostiadi, D. P. Analysis of botnet attack communication pattern behavior on computer networks. Int. J. Intell. Eng. Syst., 15(4). (2022).
Pittman, J. M. Machine learning and port scans: A systematic review. ArXiv Preprint arXiv: 230113581. (2023).
Adiwal, S., Rajendran, B. & Sudarsan, S. D. DNS intrusion detection (DID)—A SNORT-based solution to detect DNS amplification and DNS tunneling attacks. Frankl. Open. 2, 100010 (2023).
Google Scholar
Dong, G. et al. Graph neural networks in IoT: A survey. ACM Trans. Sens. Netw. 19(2), 1–50 (2023).
MATH Google Scholar
Lo, W. et al. E-graphsage: A graph neural network based intrusion detection system for iot. NOMS 2022–2022 IEEE/IFIP Network Operations and Management Symposium. IEEE, (2022).
Tran, D. H. & Park, M. Graph embedding for graph neural network in intrusion detection system. In International Conference on Information Networking (ICOIN). IEEE (2024).
Lo, W. et al. E-graphsage: A graph neural network based intrusion detection system for iot. In NOMS 2022–2022 IEEE/IFIP Network Operations and Management Symposium. IEEE (2022).
Pujol-Perich, D. et al. Unveiling the potential of graph neural networks for robust intrusion detection. ACM SIGMETRICS Perform. Evaluation Rev. 49(4), 111–117 (2022).
Google Scholar
Protogerou, A., Papadopoulos, S., Drosou, A., Tzovaras, D. & Refanidis, I. A graph neural network method for distributed anomaly detection in IoT. Evol. Syst. 12(1), 19–36 (2021).
Google Scholar
Bhavsar, M., Roy, K., Kelly, J. & Olusola, O. Anomaly-based intrusion detection system for IoT application. Discov. Internet Things. 3(1), 5 (2023).
MATH Google Scholar
Azam, Z., Islam, M. M. & Huda, M. N. Comparative analysis of intrusion detection systems and machine learning based model analysis through decision tree. IEEE Access. (2023).
Doghramachi, D. F. & Ameen, S. Y. Internet of things (IoT) security enhancement using XGboost machine learning techniques. Comput. Mater. Contin. 77(1). (2023).
Hammood, B. A. K. & Sadiq, A. T. Ensemble machine learning approach for IoT intrusion detection systems. Iraqi J. Comput. Inf. 49(2), 93–99 (2023).
MATH Google Scholar
Bilot, T., El Madhoun, N., Agha, A., Zouaoui, A. & K., & Graph neural networks for intrusion detection: A survey. IEEE Access. 11, 49114–49139 (2023).
Google Scholar
Zakariah, M., AlQahtani, S. A., Alawwad, A. M. & Alotaibi, A. A. Intrusion detection system with customized machine learning techniques for NSL-KDD dataset. Comput. Mater. Contin. 77(3). (2023).
Zhong, M., Lin, M., Zhang, C. & Xu, Z. A survey on graph neural networks for intrusion detection systems: Methods, trends and challenges. Comput. Secur., 103821 (2024).
Tran, D. H. & Park, M. Graph embedding for graph neural network in intrusion detection system. In 2024 International Conference on Information Networking (ICOIN) (pp. 395–397). (2024).
Güney, H. Preprocessing impact analysis for machine learning-based network intrusion detection.Sakarya Univ. J. Comput. Inform. Sci. 6(1), 67–79 (2023).
Gopi, R. et al. Intelligent intrusion detection system for industrial internet of things environment. Comput. Syst. Sci. Eng., 44(2). (2023).
Liu, J., Kantarci, B. & Adams, C. Machine learning-driven intrusion detection for Contiki-NG-based IoT networks exposed to NSL-KDD dataset. In Proceedings of the 2nd ACM Workshop on Wireless Security and Machine Learning (pp. 25–30). (2020).
Wu, Y. et al. Intrusion Detection for Internet of Things: an anchor Graph Clustering Approach (IEEE Transactions on Information Forensics and Security, 2025).
Amiri, Z., Heidari, A., Navimipour, N. J., Esmaeilpour, M. & Yazdani, Y. The deep learning applications in IoT-based bio-and medical informatics: A systematic literature review. Neural Comput. Appl. 36(11), 5757–5797 (2024).
Google Scholar
Iglesias Perez, S. & Criado, R. Increasing the effectiveness of network intrusion detection systems (nidss) by using multiplex networks and visibility graphs. Mathematics 11(1), 107 (2022).
MATH Google Scholar
Ahanger, A. S., Khan, S. M. & Masoodi, F. S. Intrusion detection system for iot environment using ensemble approaches. In 2023 10th International Conference on Computing for Sustainable Global Development (INDIACom) (pp. 935–938). IEEE. (2023).
Download references
The authors declare no conflict of interest.
Department of Computer Science, University of Kashmir, Srinagar, Jammu & Kashmir, India
Aamir S. Ahanger, Sajad M. Khan & Faheem Masoodi
Department of Electrical/Electronics and Computer Engineering, Afe Babalola University, Ado- Ekiti, Nigeria
Ayodeji Olalekan Salau
Saveetha School of Engineering, Saveetha Institute of Medical and Technical Sciences, Chennai, Tamil Nadu, India
Ayodeji Olalekan Salau
PubMed Google Scholar
PubMed Google Scholar
PubMed Google Scholar
PubMed Google Scholar
Aamir S Ahanger: Methodology, Performed experiments, Software, Visualization. Sajad M Khan: Conceptualization, Writing- Original draft preparation, Validation. Faheem Masoodi: Methodology and Writing- Reviewing and Editing, Validation. Ayodeji Olalekan Salau: Data curation, Investigation, Methodology and Writing- Reviewing and Editing, Validation.
Correspondence to Ayodeji Olalekan Salau.
The authors declare no competing interests.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
Reprints and permissions
Ahanger, A.S., Khan, S.M., Masoodi, F. et al. Advanced intrusion detection in internet of things using graph attention networks. Sci Rep 15, 9831 (2025). https://doi.org/10.1038/s41598-025-94624-8
Download citation
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-025-94624-8
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Advertisement
© 2025 Springer Nature Limited
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.


More Stories
A Deep Dive Into the GreedyBear Attack – CircleID
Remarks by Dr. Rajiv J. Shah at the Global Africa Business Initiative’s “Unstoppable Africa” Convening – The Rockefeller Foundation
IOT Data Hackathon 2025, Sparkling Innovation through Real-World Data, Technology and Cross-Sector Collaboration – PR Newswire